Admins and owners of WordPress websites are urged to immediately apply the Jetpack 7.9.1 critical security update to prevent potential attacks that could abuse a vulnerability that has existed since Jetpack 5.1.
You can update your installation to the 7.9.1 version through your dashboard, or manually download the Jetpack 7.9.1 release here.
Jetpack is an extremely popular WordPress plugin that provides free security, performance, and site management features including site backups, secure logins, malware scanning, and brute-force attack protection.
Not yet exploited in the wild
The vulnerability was found in the way Jetpack processed embed code and Adham Sadaqah was the one credited for responsibly disclosing the security issue.
While not a lot of details were disclosed regarding the security flaw to protect the sites that haven’t yet updated, the announcement made by Jetpack says that the bug impacts all versions starting with the 5.1 release and going back as far as July 2017.
The Jetpack developers state that no evidence was discovered until the release of the critical Jetpack 7.9.1 security update that the vulnerability has been exploited in the wild.
“However, now that the update has been released, it is only a matter of time before someone tries to take advantage of this vulnerability,” the developers warn.
The development team also says that they worked with the WordPress.org Security Team to release patches for every version of Jetpack since 5.1 and that “most websites have been or will soon be automatically updated to a secured version.”
Millions already patched
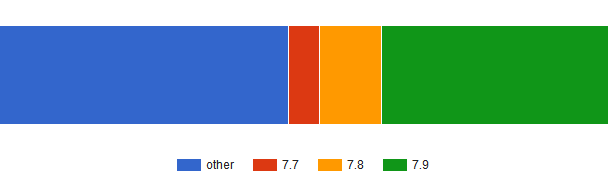
At the moment over four million out of the more than five million WordPress websites that use Jetpack have already been updated according to its entry on the WordPress Plugins site.
Jetpack received another security update to address an issue found during an internal audit of the Contact Form block in December 2018, and a critical security update patching a vulnerability in the way some Jetpack shortcodes were processed in May 2016.
Last year, hackers also found a method of installing backdoored plugins on WordPress websites using weakly protected WordPress.com accounts and the Jetpack plugin’s remote management feature.
Source: www.bleepingcomputer.com